What is Incident Response and Forensics?
As more digital data is created, stored, and shared, the threat of information being compromised increases. Today, companies and organizations need to be more vigilant than ever, both in protecting their assets and how they should react when - not if - they experience a cybersecurity incident.
Amidst the COVID-19 global pandemic - which increased reliance on the cloud, collaborative software, online transactions, and digital communication - cybercrime has increased 600%, according to PurpleSec. Additionally, the Identity Theft Resource Center revealed that data breaches were up by 38% in the second quarter of 2021 - and it anticipates the number of leaks will hit an all-time high by the end of the year.
As a result, the demand for incident response professionals is expected to grow.
What is Incident Response?
Incident response is the technical term that describes how an organization handles or manages a cyber attack or data breach. Events that disrupt operations or result in data loss – that impact the confidentiality, integrity, or availability of information systems – are categorized as incidents.
Most organizations use incident response plans to respond to and recover from security incidents, such as denial of service (DoS) attacks. The specifics of an incident response plan vary based on the incident, industry, and/or individual organization.
For a more technical answer to “what is an incident response plan,” the National Institute of Standards and Technology (NIST), defines incident response as: “the mitigation of violations of security policies and recommended practices.”
NIST, a division of the U.S. Department of Labor, published a Computer Security Incident Handling Guide that outlines how to establish and operate incident response capabilities. Within this robust guide are best practices for implementation and execution of an effective and efficient incident response plan. For starters, NIST explains all plans should feature these elements:
- Mission
- Strategies and goals
- Senior management approval
- Organizational approach to incident response
- Communication methods, internal, and external
- Metrics for measuring effectiveness
- Road map for maturity of incident response capability
- How the program fits into the overall organization
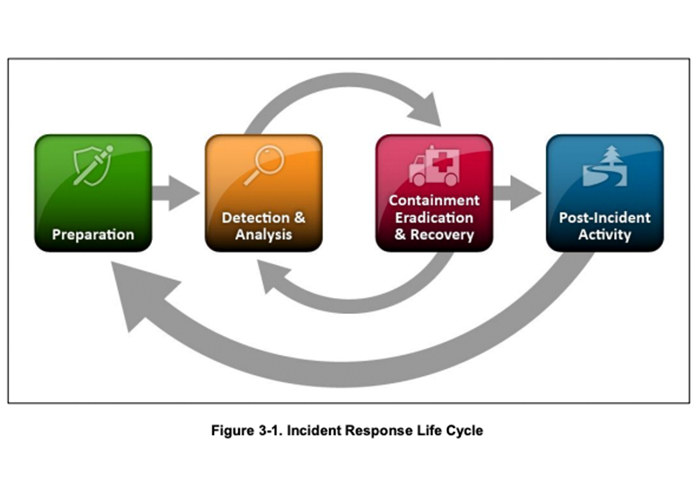
NIST defines the phases of response as:
- Preparation
- Detection and analysis
- Containment, eradication, and recovery
- Post-incident activity
These phases are often viewed as more of a lifecycle; for example, the NIST diagram below shows how the detection and containment steps can cycle back and forth before an incident is over. Additionally, post-incident activity can loop back to the preparation stage, as the experience can inform changes to the plan.
(Special Publication 800-61, Rev 2)
While any business or organization dealing with sensitive data should have an incident response plan, NIST requires a formal incident response capability for any organization that contracts with the federal government. To develop and implement an effective incident response plan, businesses and organizations require knowledgeable incident response professionals with appropriate skill sets.
Career Demand & Salary: Incident Response Analyst
While companies can mitigate risk by identifying vulnerabilities and patching them and securing information systems, it’s nearly impossible to prevent everything. Events can quickly turn into incidents that require deployment of an incident response team composed of analysts and digital forensics experts. NIST describes three staffing models for building teams: employees, partially outsourced, or fully outsourced.
What Does an Incident Response Analyst Do?
According to the Cybersecurity & Infrastructure Security Agency (CISA), there are a range of job titles assigned to the professionals who work in incident response: incident responder, incident handler, incident response engineer, incident response strategist, intrusion analyst, and perhaps the most common, incident response analyst.
While position titles and job duties can vary from company to company, generally, an incident response analyst’s day-to-day work might include:
- Monitoring security logs Investigating and triaging detections
- Collecting intrusion artifacts (such as malware, trojans, and source code)
- Assessing incidents (scope, urgency, etc.)
- Communicating findings to relevant parties
- Writing and sharing reports
- Documenting processes and procedures
Responsibilities (and pay) are likely to increase with more experience. For example, a senior or lead incident responder may be tasked with managing other team members, training new hires, and acting as a liaison to other departments.
What is the Career Outlook for Incident Response Analysts?
Information security-related careers have been on the rise for some time and, according to CEPro, this maturing industry is set to be worth more than $400 billion by 2027. A growing industry means a growing need for skilled professionals.
The U.S. Bureau of Labor Statistics (BLS) doesn’t track the specific title of “incident response analyst.” In looking at the broader field of information security, we can glean that the career outlook is largely positive for the information security sector.
The BLS expects the need for information security analysts to grow by 33% through 2030, which is much faster than the average growth for all occupations, and the median annual salary in May 2021 was $103,590. Keeping career advancement in mind - with a median annual wage of $151,150 - computer and information systems manager positions are expected to increase in demand as well through 2030.
The occupation of information security analyst ranks well in national surveys due to high demand and earning potential. It came in at #4 Best Technology Job and #10 Best STEM Job in U.S News and World Report’s annual job report and at #15 on its 100 Best Jobs list for 2021.
How Do You Get into Incident Response and Forensics?
Like many tech careers, incident response requires specialized knowledge and expertise. Skills can be developed in a variety of ways, and a degree in cybersecurity, information security, or digital forensics is a good place to start. You can also gain real-world experience in the field.
Top Skills for Incident Response Analysts & Forensic Specialists
The NIST, in its incident response handbook, explains, “...the breadth and depth of knowledge required varies based on the severity of the organization’s risk.” Some of the sought-after characteristics of incident response analysts are:
- Strong analytical and troubleshooting skills
- Extensive knowledge of operating systems
- Understanding of network and web protocols
- Deep understanding of core (and current) cybersecurity technologies
- Experience with host-level scripting
- Familiarity with frameworks such as Cyber Kill Chain and ATT&CK
- Experience with cloud environments
- Knowledge of industry-relevant regulations
Incident response analysts must be well-versed in the life cycle of cybersecurity threats and attacks - and committed to keeping up to date on the latest technologies.
Experience and Education Needed for Incident Response Analyst Careers
The education you need to become an incident response analyst is, typically, a minimum of a bachelor’s degree in a computer or technology-related program, such as cybersecurity, digital forensics, or computer information systems.
Often, a four-year degree isn’t enough. Experience, continued education, and industry certifications may be required depending on the position to demonstrate knowledge and technical competencies. If you’re looking to advance in the field, management and executive-level positions in incident response often require a master’s degree or higher.
The master’s of information technology at Champlain College Online (CCO) offers three specializations, including digital forensics and incident response. This concentration - which leads to a graduate certificate on top of the master’s degree - was developed in response to industry demand for IT professionals with expanded skills in risk management and digital investigations. CCO also offers master’s degrees in digital forensic science and information security.
CCO has been designated as a National Center of Academic Excellence in Cyber Defense Education by the U.S. National Security Agency and the Department of Homeland Security.
Curious about our tech-related programs? Learn more.
Request Information
Connect with our admissions team to learn more about Champlain College Online.

Request Information
I acknowledge that, by clicking the "submit" button, I am giving my express written consent to Champlain College and its representatives to contact me about educational opportunities via email, text, or phone, at the phone number above, including my mobile phone, using an automatic dialer, or pre-recorded message. Message and data rates may apply. I understand that my consent is not a requirement for enrollment, and I may withdraw my consent at any time.